There exist many protocols through which the internet functions and each layer of the TCP/IP archetecture has its own protocols, each serving its own specific function
Application layer
The majority of the protocols that we know are on the application layer, the one that is closer to the user and works with the ways the client software interprets them
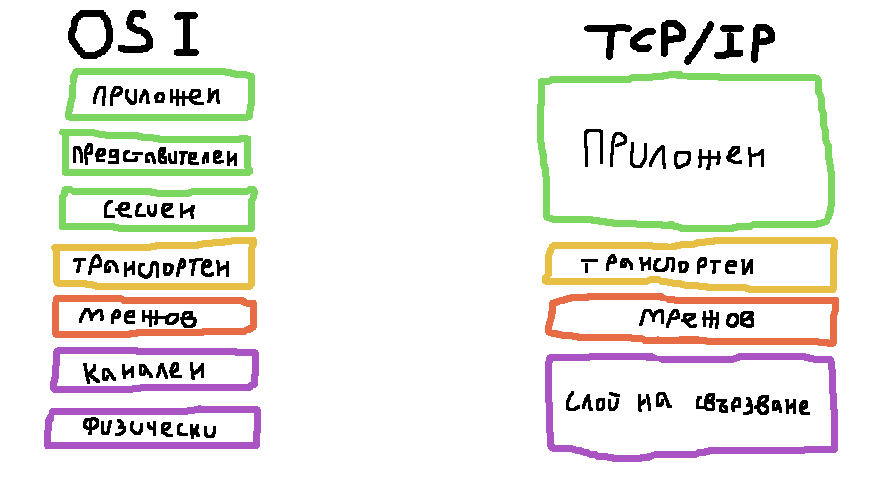
As the TCP/IP architecure is somewhat different from the OSI model and has less layers, application layer in TCP/IP corresponding to application-presentation-session layers in OSI
HTTP(S)
To begin with HTTP(S), the protocol known to all, which is used for transfer of hypertext documents.
For that purpose it does not need much complexity in itself
The client sends requests and the server responds

These requests are usually a specific method + URI (universal resource indicator, not to be confused with URL, universal resource loader, which is one of URI types), and these methods can be:
- GET - retrives data from a specific URI
- HEAD - retrieves just the header of the response
- POST - asks the server to accept an included file to the URI, used on forums, newsgroups, etc.
- PUT - creates or modifies an URI
- DELETE - removes a resource
- TRACE - asks the server to resend the last request back to trace changes made by intermediate servers
- OPTIONS - lists methods the client is allowed to do with a specific resource
- PATCH - applies partial changes
HTTPS is HTTP with added encryption.
A website is protected with an SSL certificate, which contains a public and a private key
The public key can only encrypt and the private can only decrypt and it's impossible to get one key from another
The server sends to the client the public key, which it then uses to encrypt the request and send it back to the server, which decrypts it with the private
gopher
Gopher was used as a predecessor HTTP in the early 90s
Unlike HTTP it uses a stricter file structure, so it can only serve images and documents one at a time and it's unsupported by most modern browsers
But despite that, some enthusiasts still use it like ham radio
You can read more about it here and through proxy.vulpes.one you can access gopherspace sites through your usual browser

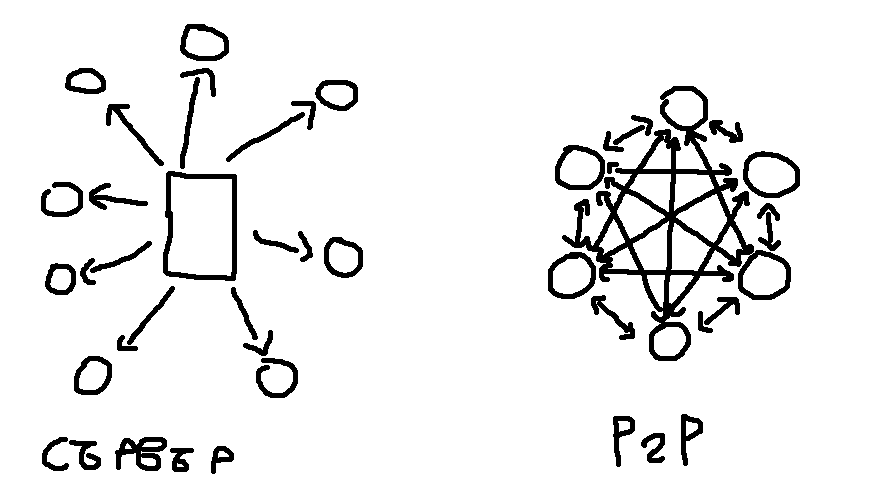
bittorrent
bittorent is a decentralized P2P protocol for transfer of large files. The P2P nature of it comes as an advantage as it allows to avoid reliance on one specific server and avoid problems relating to a singular server's bandwidth or availability
Despite many people associating it with piracy, it is used not only in that. Many legal streaming services, video game updates and even researchers when they need to transfer a large dataset use it too.
Whois
Query protocol for obtaining data about an IP address/domain naime
Misc.
Various mail and messaging protocols, various specific protocols used in hospitals/banks/etc.
Transport layer
The two main protocols in the transport layer are TCP and UDP
TCP is focused on the integrity of the information, double-checking with the server if a packet arrived completely intact and re-requests it if needed
UDP, on the contrary, focuses on speed and does not check the packets. It is used when speed is more important than quality, such as VOIP, gaming or livestreaming
Packet loss in TCP is a loss of speed, packet loss in UDP is a loss of quality
Network layers
The network layer has IPv4 and IPv6
IP, in a nutshell, is like a zip code of a computer in a network
Each sent packet gets a IP-header so the downstream servers know where to send it
The difference between the two is that v6 has more available addresses than v4
v4 consists of 4 bytes and has only 4.2 billion combinations, example: 91.139.146.41
v6 has eight groups of four bytes, giving 3.4×10^38 total combinations, example: 2001:0db8:0000:0000:0000:8a2e:0370:7334
The first half of a v4 address is the network number, the second is the host number. For each host on the same network, the network number is the same but the host numbers are different.
Some networks may also be divided into subnets, which allocates some numbers from the host to the network
Link layer
The bottom layer of TCP/IP architecture. Deep abyss that even I don't understand well
MAC addresses (medium access control, not to be confused with Apple's Mac, McDonalds' Mc or my nonbinary friend Mack who makes chiptune)
Unlike IP addresses, which identify an address in a network, MAC addresses identify only singular computer and are always static. Two laptops on the same wifi will have the same IP but different MAC addresses
Example: 00:A0:C9:14:C8:29
They are used in non-IP communication of devices, such as a bluetooth link or a 2ifi router-to-device link
